I'm always excited to take on new projects and collaborate with innovative minds.
Tokyo Japan
I'm always excited to take on new projects and collaborate with innovative minds.
Tokyo Japan
Instead of every team running its own CI, clusters, and infrastructure, companies now consolidate into multi-tenant platform engineering ecosystems

As engineering platforms scale, you reach a stage where multiple teams, departments, or even customer groups must share the same infrastructure — especially in:
Cloud-native SDV platforms
Kubernetes-based developer platforms
Simulation/VDK workloads
CI/CD ecosystems
Data engineering environments
A multi-tenant platform allows the same underlying infrastructure to be safely shared by multiple tenants while ensuring:
✔ Zero data leakage
✔ Predictable performance
✔ Controlled resource usage
✔ Per-team cost management
✔ Independent deployments
✔ Secure isolation
✔ Consistent governance
This guide provides a full architectural & implementation blueprint for building a secure, scalable multi-tenant DevOps platform.
Multiple teams → one platform
Avoid platform duplication
Reduce operational overhead
Shared DevOps capabilities
Prevent cross-team data exposure
Ensure tenants cannot see/affect each other
Consistent CI/CD
Shared observability
Central governance
Multi-tenancy is a core requirement for any enterprise digital engineering environment.
Teams share:
Namespace
Resources
Logs
Security = basic
Good for hobby/dev only.
Each team has:
Dedicated namespaces
Strict RBAC
Network policies
Resource quotas
Isolated dashboards
This is the recommended model for enterprise SDV platforms.
Used in:
Automotive
Healthcare
Finance
Includes:
Workload identity
Encryption boundaries
Policy-as-code
Dedicated API rate limits
Here is a proven architecture used for enterprise cloud platforms:
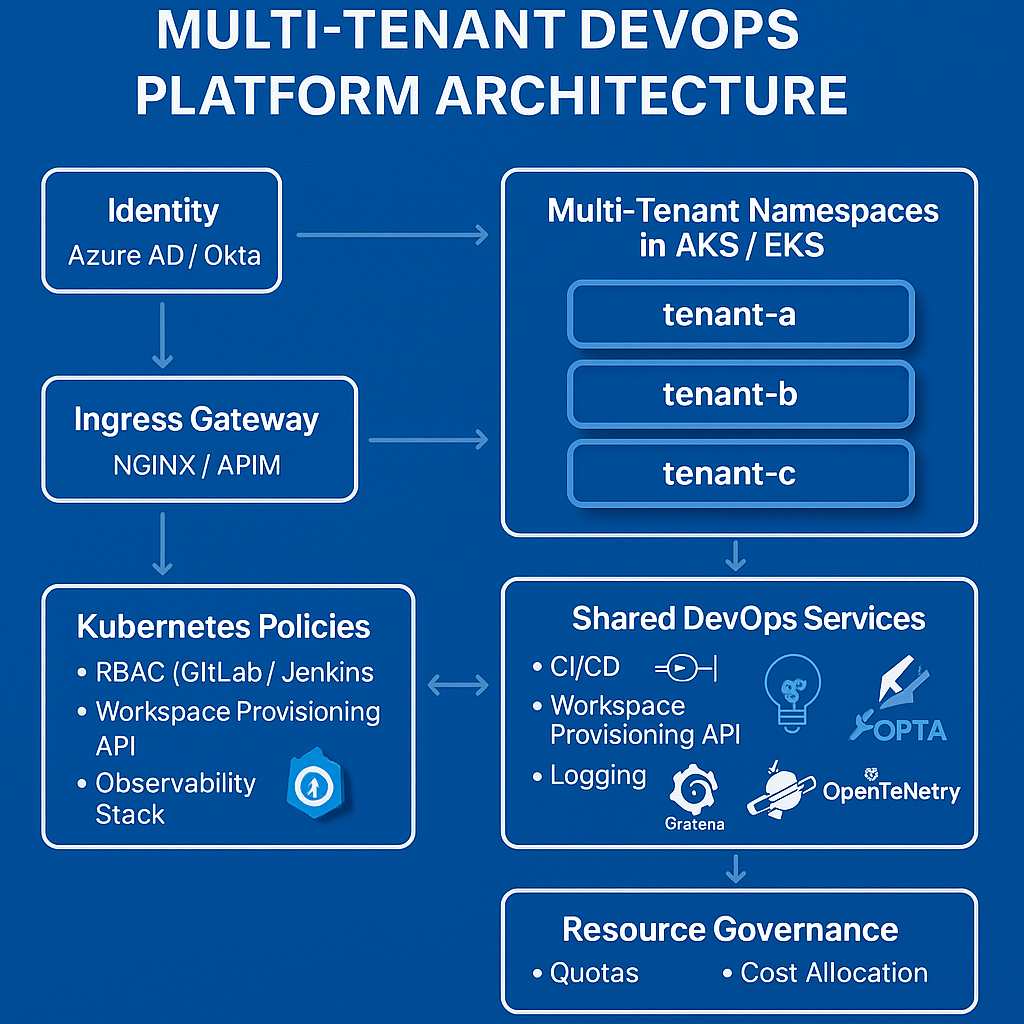
This keeps tenants isolated while reusing the underlying cluster.
Each tenant (team/project/customer) must get:
Example roles:
Developer
DevOps
Viewer
Block access to other namespaces.
Control usage:
Unique API paths:
This ensures clean separation.
Use:
Developers from Tenant A cannot touch Tenant B.
Example: block cross-namespace traffic:
Block misconfigurations:
Privileged containers
HostPath volumes
Duplicate namespaces
Prevent dangerous workloads.
Assign default CPU/memory per pod.
This prevents noisy-neighbor issues.
CI/CD pipeline must:
Identify tenant
Use tenant-specific values files
Deploy to correct namespaces
Enforce access patterns
GitOps makes this easier by isolating deployments.
Use:
Grafana multi-tenant dashboards
Azure Monitor queries filtered by namespace
Loki log stream filters
API-level usage dashboards in API-M
Each tenant sees only their data.
API-Management (APIM) acts as boundary:
Per-tenant authentication
Custom request headers
Rate-limit rules
RBAC access
JWT validation
This guarantees fair usage.
Platform exposes APIs like:
Workspaces run inside tenant namespaces with:
Resource limits
Network isolation
Log redaction policies
Use:
Dedicated PVC
Separate blob containers
Access policies based on tenant
Encryption keys per tenant (optional)
Use KubeCost or custom dashboards.
Metrics per tenant:
CPU usage
Memory usage
Node hours
Storage usage
API calls
Pipeline runs
This improves budget planning.
Automate cleanup:
Delete namespaces
Recycle PVCs
Remove access control
Archive logs
Reclaim external resources
Developer pushes code
Tenant-specific CI pipeline runs
GitOps updates tenant Namespace
ArgoCD syncs only Tenant A resources
RBAC ensures access only to Tenant A
API-M enforces tenant-specific policies
Dashboard shows only Tenant A traces
Cost allocation updated
Tenant B remains fully unaffected.
✔ Use Azure AD for identity
✔ Separate K8s namespaces
✔ OPA policies for governance
✔ Encryption on storage
✔ Enable cluster autoscaling
✔ Keep logs tenant-segregated
✔ Implement FINOPS dashboards
✔ Soft-delete tenant data
✔ Keep 30-day retention
✔ Lock down public endpoints
✔ Provide templates per tenant
✔ Use golden-path CI/CD structures
❌ Shared namespace across tenants
❌ Shared secrets or configmaps
❌ No RBAC policies
❌ Logs accessible from other teams
❌ Incorrect resource quotas
❌ Mixing API paths without identifiers
Avoid these to maintain security & stability.
A secure multi-tenant DevOps platform is one of the most critical engineering investments a company can make.
When implemented correctly, it delivers:
High security
Predictable performance
Cost governance
Seamless developer onboarding
Stable shared infrastructure
Per-tenant isolation
Enterprise-grade compliance
This architecture is now a must-have for cloud-native SDV platforms, automotive engineering clouds, and any large-scale DevOps environment.
Your email address will not be published. Required fields are marked *